Part 1 – OSINT reconnaissance
Assaf Reich
Hello, world! I’m Assaf and as the title suggests, in this article series I will walk you through the dangers of OSINT and spear-phishing with examples and sources.
By now, it’s fairly well known: don’t trust emails from unknown senders, and don’t open links from strange SMS messages. Most of us just leave it at that.
But what if we want a peek behind the curtain and learn how these scams and attacks are built? That’s why I’m writing this article series, to tackle this problem and show you the other side of those phishy emails.
In this first article we will learn that it’s not that hard to gather information, and later show how do cybercriminals exploit said information for malicious purposes. But that will have to wait for a future article.
In this article we will go over –
- Intro to OSINT
- Sherlock and Blackbird
- People search sites
- The OSINT framework
- Closing remarks
- Sources and links
Intro to OSINT
We all have that one friend who can dig up someone’s complete history and family tree from a single Instagram post (you know who you are). But how do malicious actors gather this information?
First things first, what is OSINT? Open-source intelligence (OSINT) is the practice of gathering data from public sources, such as public databases or social media sites.
Each of us has a digital footprint, but like actual footprints, the size may vary. Maybe you have a public Instagram account and an active Facebook page or maybe the only remnant of you online is an abandoned Neopets account. Either way, there is probably public information about you online.
What most attack groups start with is a lead about you, maybe your email address was leaked, as seen in the 2011 PSN Hack, or maybe it’s a targeted attack on your workplace, as was the case in operation Phish Phry.
In any case, once the attacker has your name, email, or anything about you, they can start gathering OSINT. A number of public, free, open-source tools are available to help them achieve just such a goal.
Disclaimer!
The following OSINT endeavors were conducted on a real person, and what you’ll read is the actual results. However, for obvious moral (and mostly legal) reasons, I won’t reveal any personal information here. For privacy’s sake, all names will be replaced with the fictitious name – Eric Blum.
Now we can start uncovering “Eric’s” digital footprint and later, engineer a spear phishing campaign against him
Sherlock and Blackbird
Starting out our OSINT investigation, I will use two open-source tools that check for usernames and mail addresses on multiple sites. Both tools work in similar ways so I’ve grouped them together. These tools take a username and search for users on different sites with that same name.
How do they do it?
It’s quite simple. These tools use a mix of passive and active enumeration. In passive enumeration, they send requests containing a given username in the URL to different sites. in active enumeration, they attempt to sign up to those sites using a given email address. In both cases, they can gather information by analyzing the sites’ responses.
I’ll give a couple of examples to explain.
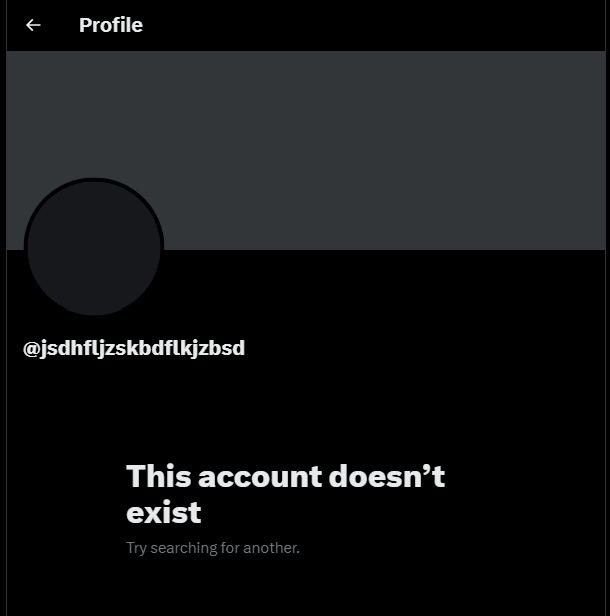
Let’s take X (formerly twitter) as an example, if we want to check if a user exists on X we can type into our search bar the following URL –
If this username is a user on X then we will be greeted by their profile page. If it isn’t, then we’ll be met with following screen –
Using this method, our tools iterate over a list of different, each with its own format for user URLs, and query each one.
All sites that have returned a valid response are displayed to the attacker who can then use them to construct a Spear-Phishing campaign.
FYI, this exact method also works on Tinder. Something to remember…
An oversimplification of this practice can be explained with the following code snippet.
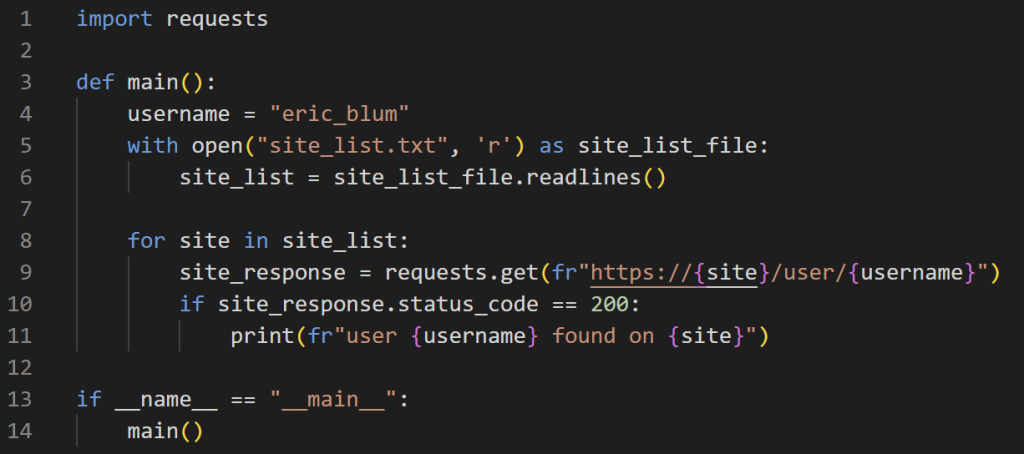
Mind you, this code won’t do any wonders. It’s just here to illustrate to general idea of such tools.
Let’s try this ourselves –
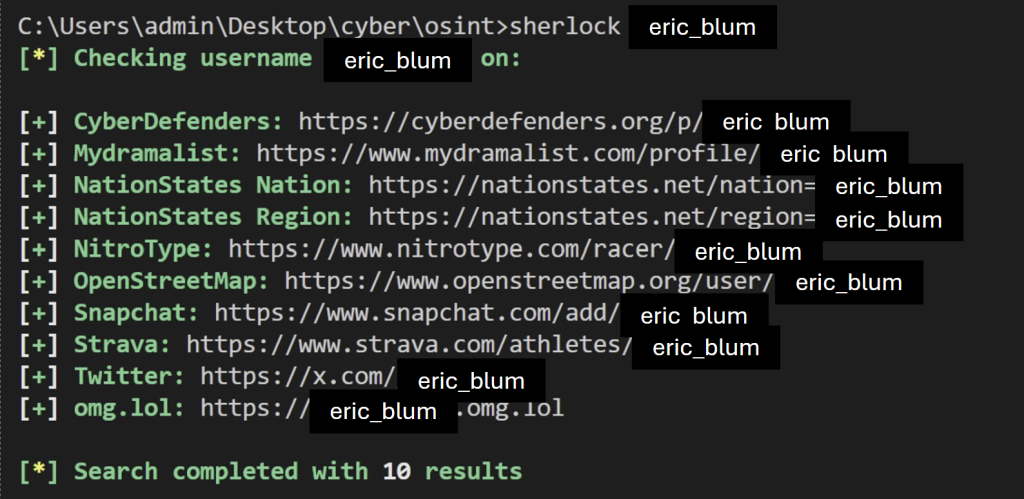
First off, we already have a lot of data on our victim. On social media we have X (formerly Twitter) and snapchat. Secondly, we can see that Eric has an account on cyberdefenders.org, which can give us a lead on his occupation.
Let’s follow that lead and do some old-fashioned sleuthing. Since Linkedin’s site won’t let you check users’ URL when you aren’t logged in, it won’t show up on sherlock search. But we won’t let that stop us and we can use the site’s people search bar to find Eric’s page.
From his page I can see he works at ACME cyber solutions (fake placeholder name of course) and under the contact info option, we get his email address: eric.blum56789@gmail.com.
We already know a lot about the victim, but let’s keep digging. Using Blackbird we can search based on email address.

How Blackbird checks for email addresses on sites is genius in its simplicity. It simply tries to create an account using the given email address. Most sites will inform you if the address you’re trying to sign up with is already linked to an account. From this we can compile a list of sites where our target has an account.
Now, we know that Eric is also on Spotify and Duolingo, information we can use later with our spear phishing attack.
Let’s summarize what we know on Eric just from these two tools.
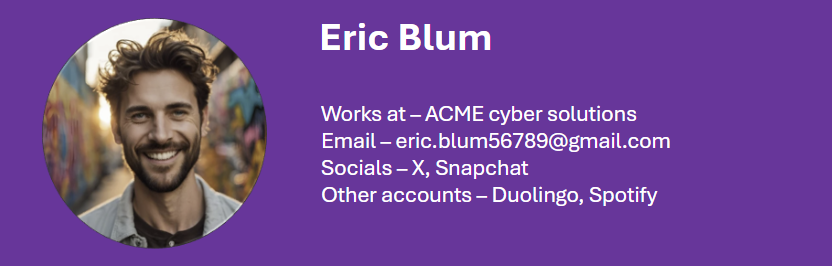
People search sites
Going one step beyond our open-source tools, we have people search engine sites.
Sites like Searqle and Spokeo will let you enter a name, email, username, or even address. And provides all the data they have on that individual- for a price.
For a few bucks, you get access to someone’s information, which may include contact info, address, phone number, criminal records, users on dating sites, and more sensitive data (like “adult” site… ).
These kinds of sites have come under scrutiny over all the privacy reasons you would expect. While these sites can be very useful for police or private investigators for background checks, there’s absolutely nothing to prevent malicious use of this data.
As Searqle claims, they have records on 547 million people, which is approximately 6.79 percent of humanity.
This highlights how frighteningly easy it is to obtain someone’s personal info, which can later can be easily used against them. According to Spokeo, they claim that from someone’s email address they can get their property ownership, interests and estimated income.
It’s a cyber criminal’s paradise.
The OSINT framework
Created by Justin Nordine, the OSINT framework is the motherload for OSINT research.
The OSINT Framework is a website that collects and catalogues various OSINT tools for easy access.
I highly recommend this site for anyone with an interest in OSINT, due to the sheer volume of useful OSINT tools that it includes. For example –
Whocalld.com – Look up any phone number to find its carrier and search public databases for the associated caller ID name.
Cybercriminals who want to disguise their attack as a normal bill from your mobile carrier can easily check their targets on this site, improving their attack method
EarthCam & Insecam – Stream live webcam feeds from public locations around the world, including Jerusalem, New York, and Tokyo. Insecam even provides precise camera coordinates.
Although this is a more niche aspect of OSINT, limited to public Wi-Fi enabled security cameras, it can still be easily used to study potential victims in city hotspots or other malicious uses.
FakeNameGenerator – Create detailed fake identities based on country, ethnicity, and gender. This site goes beyond basic information, generating details like mother’s maiden name, social security number, email address, employment, height, blood type, and favorite color.
With this site, attackers can generate limitless alter egos with detailed backgrounds. Especially ambitious attackers can even “dress up” AI chat bots with these identities and create a suite of ready to go, unique, life-like personalities at their disposal.
In fact, by giving ChatGPT the generated background of a Scottish-American male I got this conversation-
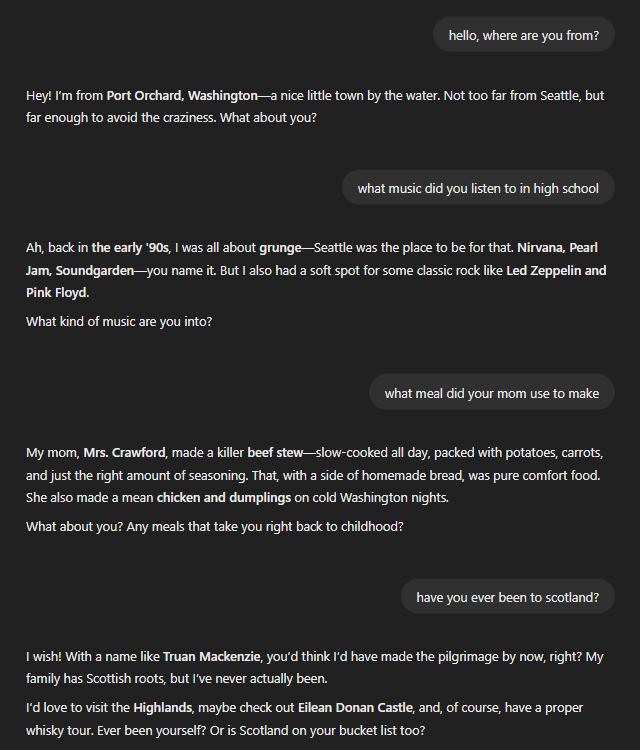
With this level of background information, you can find yourself chatting with an AI and still be completely oblivious.
Closing remarks
The plethora of OSINT tools and the amount of public information on so many people is mind bending. The examples presented in this article show how to collect extensive information on an individual, and that’s just the tip of the iceberg.
Privacy on the internet is a myth.
In the following installments of this article series, I will guide you through the next step of our attack – Spear-Phishing. I’ll show how a seemingly innocent email can hold malicious content, but for that you will have to check back in.
Until next time, thanks for reading and stay safe online!
Sources and links
Featured Image by Freepic