Introduction
Phishing attacks have long been the primary entry point for cybercriminals, but today, attackers are evolving beyond traditional email scams. Social engineering attacks are becoming more psychologically sophisticated, bypassing standard defenses and directly targeting human vulnerabilities.
One recent case involved a multi-million dollar theft orchestrated entirely over a Zoom call– where an attacker posed as an executive, tricking employees into transferring funds.
Why Current Defenses Are Failing
Gartner research predicts that by 2025, over 70% of organizations will have suffered from social engineering attacks that bypass technical controls.
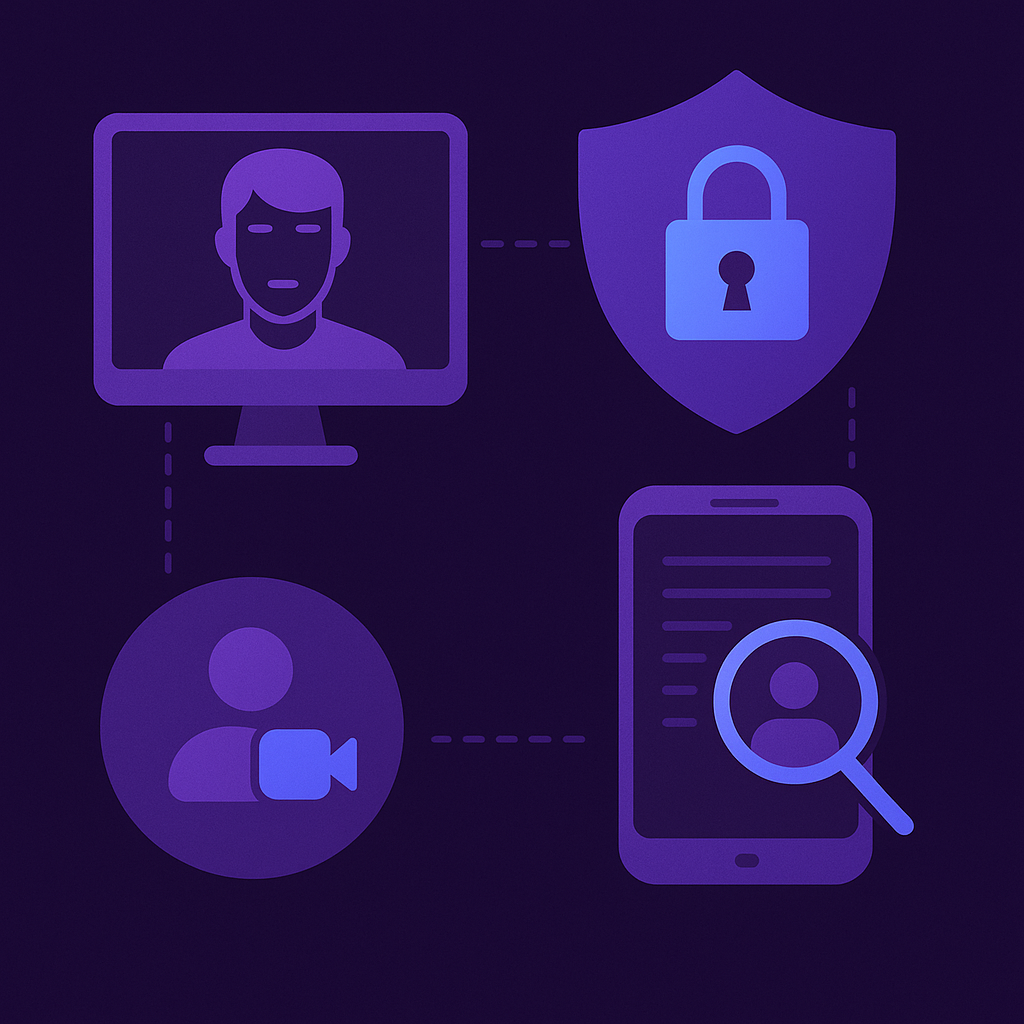
Social engineering techniques now extend beyond phishing emails into business communication platforms like:
- Zoom & Teams – Attackers use deepfake video/audio to impersonate executives.
- WhatsApp & Slack – Fake messages from trusted colleagues requesting financial transactions.
- CRM & Customer Support Systems – Manipulating customer service agents into providing access.
The New Frontier: AI-Driven Social Engineering
Cybercriminals are leveraging Natural Language Processing (NLP) to mimic writing styles, predict human responses, and craft near-perfect impersonations.
This is where Cyvore’s Data Analysis NLU (DAN) engine is a game-changer. Unlike traditional phishing detection, DAN analyzes:
Psychological Manipulation Tactics
Real-Time Behavioral Patterns
Threat Indicators Across Multiple Communication Channels
For CISOs, the message is clear: phishing is no longer just about fraudulent links. Social engineering has evolved, and so should your cybersecurity strategy.
References:
CISA. “Avoiding Social Engineering and Phishing Attacks.”
CNN. “Finance worker pays out $25 million after video call with deepfake ‘boss’.”
Gartner via Wards Auto. “Gartner Predicts Highs and Lows of AI in Cybersecurity.”
Zscaler. “8 Cyber Predictions for 2025: A CSO’s Perspective.”