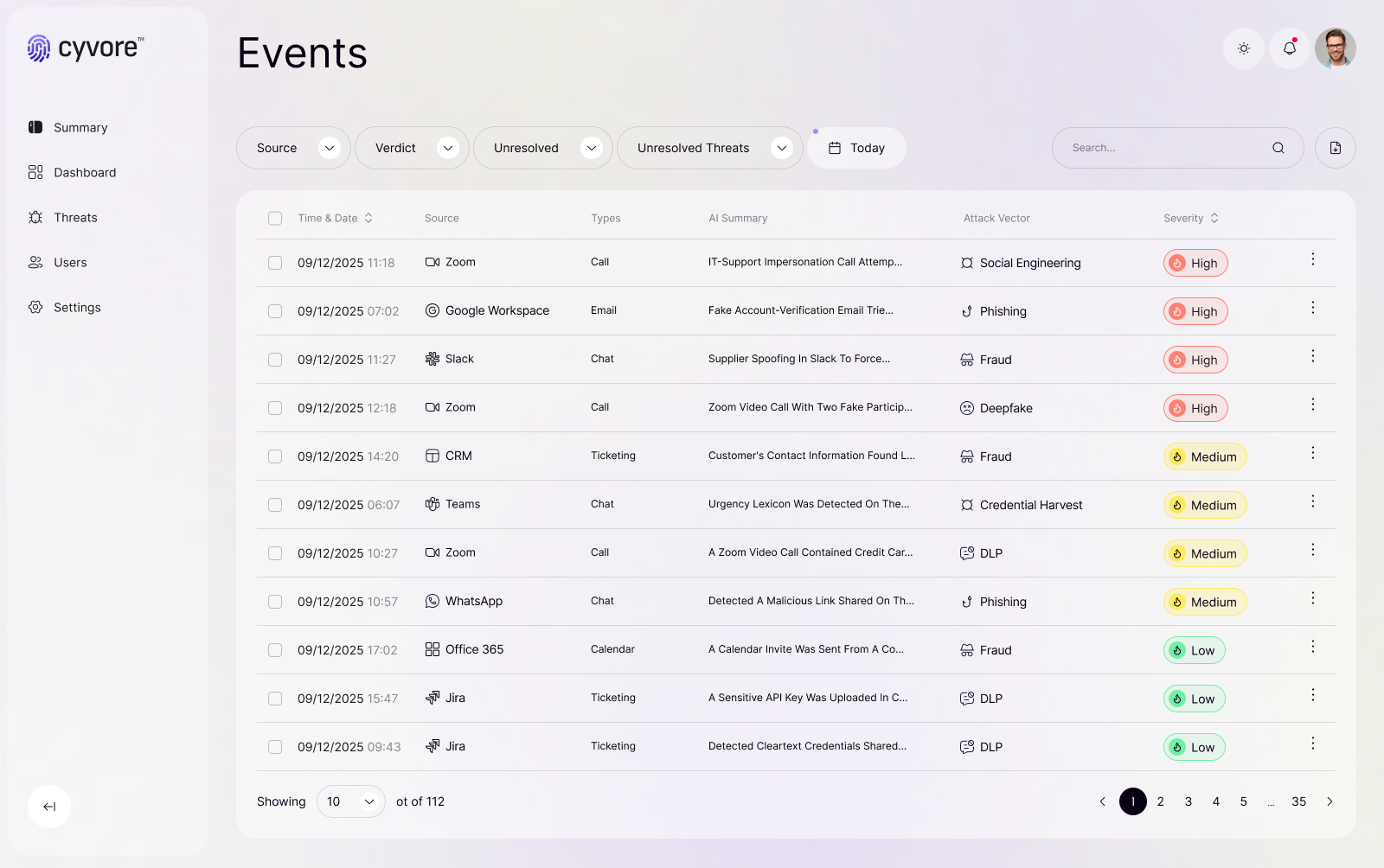
AI-Driven Threat Intelligence for
a Secure Digital Workspace
Proactive Threat Detection
Cyvore combines cutting-edge AI, machine learning, and behavioral analytics to detect and investigate threats.
Real-Time Threat Response
Cyvore uses advanced automation and intelligence to contain and neutralize threats before they impact your organization.
Cyvore’s Core Security Technologies
From phishing detection and unique proactive threat intelligence monitoring to behavior analysis and seamless stack integration, Cyvore delivers multilayered protection that stops threats before they impact your organization.
OPR
Optical Phishing
Recognition
- AI-powered visual scanning that detects phishing attempts, impersonation, and fraud campaigns.
- Stops zero-day phishing threats invisible to traditional engines.
- Identifies deceptive use of logos, fonts, and layouts.
- Mimics human visual perception to expose threats missed by standard systems.
TIAO
Threat Intelligence
Autonomous Operation
- Monitors underground markets to spot compromised credentials in real time.
- Detects enterprise data leaks across dark web and unauthorized repositories.
- Investigates Indicators of Compromise (IOC) with automated intelligence.
- Proactively traces and disrupts malicious actors behind ongoing campaigns.
DAN
Data Analysis NLU
Engine
- Uses Natural Language Understanding (NLU) to detect fraud and social engineering.
- Reveals manipulation tactics in scams and insider threats.
- Identifies subtle behavioral cues that indicate possible breaches.
- Strengthens defense by exposing psychological vectors of attack.
Seamless Integration with Existing Security Stacks
Seamless Integration, works effortlessly with firewalls, endpoint security (EDR), and SIEM tools to strengthen and simplify your cybersecurity.
Native Integration Across Security Platforms
Easily connects with your current security tools for smoother, faster protection.
Smart Security
Enhances existing security infrastructure with real-time fraud detection and active threat investigation.
Seamless Integration
Works effortlessly with firewalls, endpoint security (EDR), and SIEM tools to strengthen and simplify your cybersecurity.
AI-Driven Threat Intelligence for a Secure Digital Workspace
Cyvore combines cutting-edge AI, machine learning, and behavioral analytics to detect, investigate, and neutralize threats before they compromise your organization.